command query responsibility segregation
In CQRS, a command is an instruction, a directive to perform a specific task. It is an intention to change something and doesn’t return a value, only an indication of success or failure. And, a query is a request for information that doesn’t change the system’s state or cause any side effects.
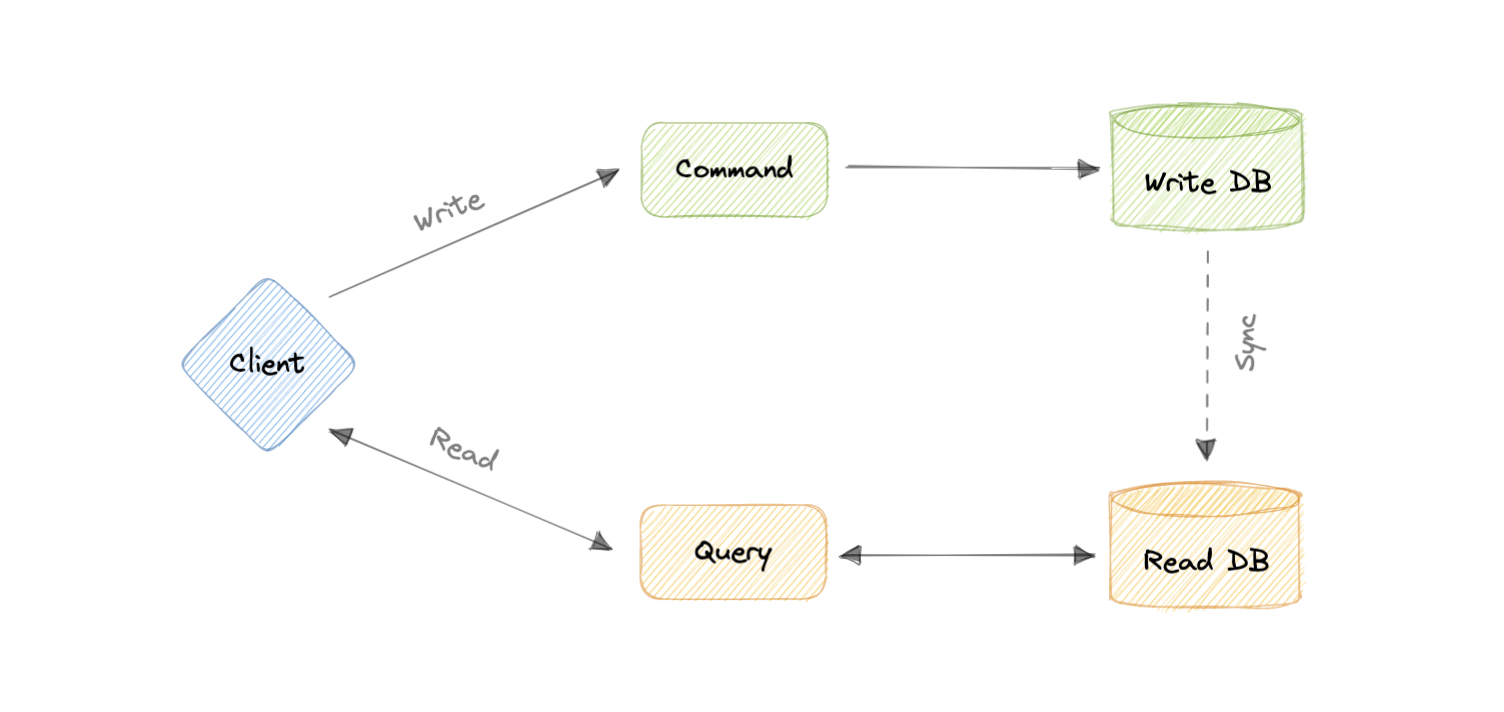
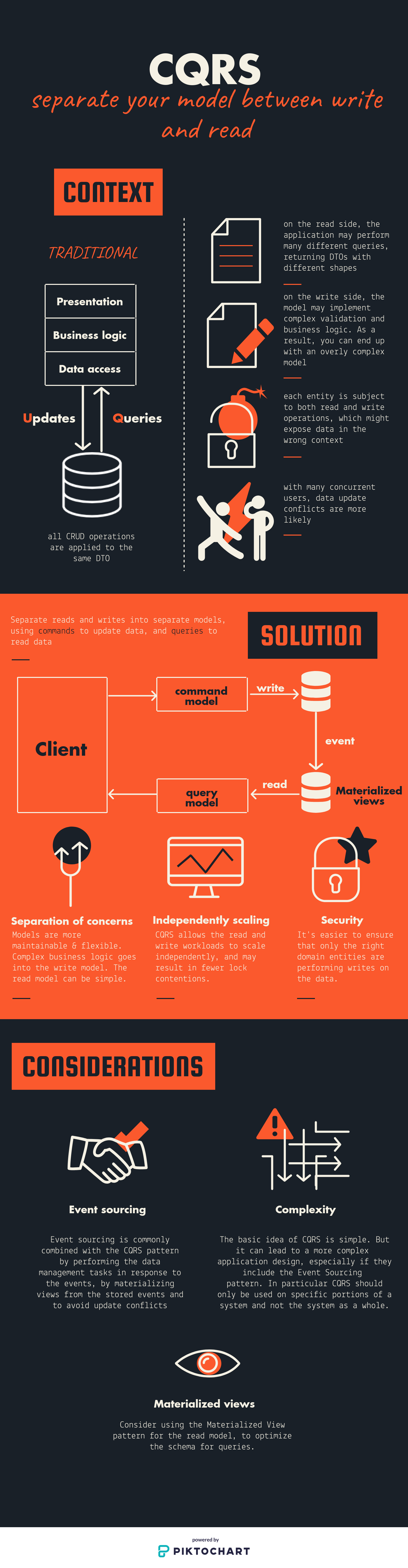
The core principle of CQRS is the separation of commands and queries. They perform fundamentally different roles within a system, and separating them means that each can be optimized as needed, which distributed systems can really benefit from.
CQRS with Event Sourcing
The CQRS pattern is often used along with the Event Sourcing pattern. CQRS-based systems use separate read and write data models, each tailored to relevant tasks and often located in physically separate stores.
When used with the Event Sourcing pattern, the store of events is the write model and is the official source of information. The read model of a CQRS-based system provides materialized views of the data, typically as highly denormalized views.
Advantages
Let’s discuss some advantages of CQRS:
- Allows independent scaling of read and write workloads.
- Easier scaling, optimizations, and architectural changes.
- Closer to business logic with loose coupling.
- The application can avoid complex joins when querying.
- Clear boundaries between the system behavior.
Disadvantages
Below are some disadvantages of CQRS:
- More complex application design.
- Message failures or duplicate messages can occur.
- Dealing with eventual consistency is a challenge.
- Increased system maintenance efforts.
Use cases
Here are some scenarios where CQRS will be helpful:
- The performance of data reads must be fine-tuned separately from the performance of data writes.
- The system is expected to evolve over time and might contain multiple versions of the model, or where business rules change regularly.
- Integration with other systems, especially in combination with event sourcing, where the temporal failure of one subsystem shouldn’t affect the availability of the others.
- Better security to ensure that only the right domain entities are performing writes on the data.